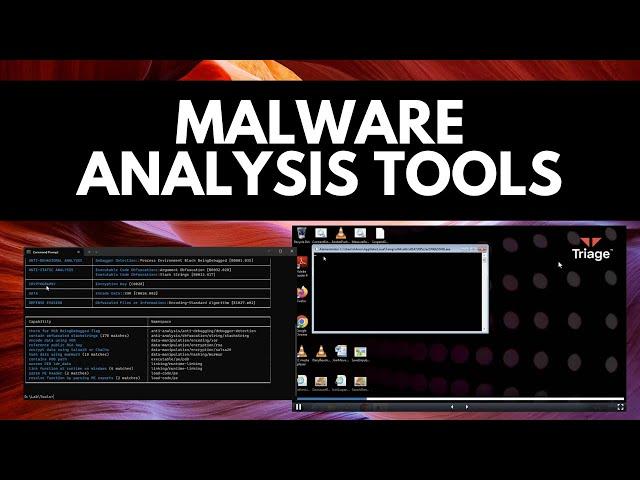
Malware Analysis Tools YOU COULD USE
Buy the best antivirus: https://thepcsecuritychannel.com/best-antivirus
Join the discussion on Discord: http://discord.tpsc.tech/
Get your business endpoints tested by us: http://tpsc.tech/
Contact us for business: https://thepcsecuritychannel.com/contact
Тэги:
#The_PC_Security_Channel #TPSC #cybersecurity #cyber_security #computer_security #internet_security #antivirus #anti_malware #ransomware #trojan #virus #PUP #best_antivirus #best_internet_security #learn_cybersecurity #hacking #hack #security #technology #cyber_insurance #cybersecurity_degree #best_EDR #EDR #malware_analysis_tools #capa #triage #malware_analysis #best_malware_analysis_toolsКомментарии:

how to acces triage vms?
Ответить
Some tools I use are Capa, bstrings, procmon, pestudio, and running things on inetsim
Ответить
Super cool!
Ответить
Can i get infected from seeing the live sandbox and get it on my main pc.
Ответить
Great video! Thank you!
Ответить
Can a virus jump over triage? (To your pc?)
Ответить
but any of these tools can anylize a simple encrypted .luac file...
Ответить
He has very good info but the vpn bullshit is annoying, I get that for a channel that is about cybersec there aren't many sponsor options but cmon a vpn doesn't do anything...encryption this encryption that literally every site is "peer to peer encrypted" or whatever their buzzword is it has never stopped anyone from doing anything ever...great advice but I see vpn ads everywhere and it's just disheartening
Ответить
Do we have any ransomware Stop djvu online ID solutions ?
Ответить
don't forget virus total
Ответить
We need a Free Open Source AI-based malware detector/remover. But, then intelligence agencies would be exposed.
Ответить
I like your vids. Quite often it’s over my head. I would like to learn how as a beginner of trying to protect my pc from outside hacks. What do you suggest how I get started? Do you have a video on how to start out? Tyvm.
Ответить
How do we know if our computer is infected with malware stealer which is 100% FUD?
Ответить
Amazing video thank you
Ответить
You got sponsored by the scummy Nord, but hopefully the viewers know that the VPN is bad
Ответить
Hey!
I was browsing the internet and i came upon ClamAV claiming to be an open source AV solution, and according to its wikipedia page it has a detection rate of 59%
Could you test it if its actually true?

There are only 2 viruses in Windows, one is Edge and the other is Defender, no matter how much you delete and block them, they download and install themselves without asking anything. 🤣
Ответить
Ahh yess, this is a great video. But TPS, how do we know what is a walware or what executable is a malware?
Ответить
Wow ! new for me, thanks !
Ответить
My friend got his many accs stolen somehow, instagram shows no logs of ips while steam showed morocco. So, we think its his google chrome cookies and possibly account (but no session exists outside his own devices as we checked), not passwords though?, but maybe the pc itself was controlled? So anyway, since he cant format rn, we had to just use many tools you mentioned. We dont know if this is enough. Do you think we should do anything extra?
Ответить
Yooo this is an amazing example of enhancing the global security posture by educating. Thank you for this set!
Ответить
HEY, HOW ABOUT LINKS TO THESE TOOLS? 🤔
Ответить
Bro I was looking for something exactly like last activity view today and couple hours later this video shows in my recommended. Thank you!
Ответить
15 hackers have seen this video so far... lol 👎
Ответить
Running Malware analysis tool into a Malware
Ответить
Nice!! Where can I get it?
Ответить
if your looking at a executable then the tool of choice is ghidra. you can also use ida pro if on windows or reflector. if your looking at network activity then wireshark works fine.
i am disappointed at the videos lack of technical ability and this is coming from someone who has very basic computer ability skills 2/10 lol.

Nir Soft freeware system tools are great! Been using them a long time.
Ответить
Imagine one day you sent a sample that could breach through the Sandbox environment. 🤔
Ответить
Mandient is owned by Google
Ответить
I have learnt a lot from you and will be learning more in the future.
Thank you!

How can I trust you with that choice of sponsor and you don't bother to link the software and websites you talk about in the description?
Ответить
My main Working Station is Virtual Machine. I refuse to do my activity on Bare Metal. VM is easy to deal if there is something went wrong. You can just Snapshot it or delete entirely and install a fresh one.
Ответить
You don't need a third-party antivirus. It is far more important to update your PC & browser. This is your first line of defence. Windows security is all you need. You don't need none of this shit!
Ответить
Great suggestions Leo. Other tools that I use when performing static analysis are Floss (FLARE Obfuscated String Solver) - which is like 'strings' on steroids. It can find encrypted/encoded strings and decode them, find interesting strings automatically (without having to grep specifically for them).
010 Editor (or WinHex, or any other hex editor) can be useful also, particularly when analysing samples that are XORed (you can find the XOR key by viewing the sample in a hex editor)
CyberChef also very useful for dealing with encoding/obfuscation.
PEiD, DIE, CFF Explorer are also valuable when analysing packed malware.
Process Explorer, Process Monitor, Fakenet, etc all good for dynamic analysis
Memory dumping, and analysis with volatility can be incredibly valuable too.
And last but not least, dnSpy, Ghidra and IDA pro for when you want to have a real headache and nothing else is working!

Leo
Ответить
Hello, how to analyze dll file. with cape... Example: Some software basically has nothing until they download a DLL file to perform their task.
Ответить
i used this tool for manipulating my frnds not in bad way ... installed on his laptop 🤣🤣 7 years back 1st tool
Ответить
Nice🥰
Ответить
Leo
Ответить
Leo
Ответить
I wish there was a website that just said what the virus did (steal passwords, lock you out of your computer, etc) instead of a bunch of random codes and saying "yeah, this is bad, but we're not gonna say why this is bad"
Ответить
Process Monitor but worse.
Ответить
This dude called the security channel is seriously plugging nord
Ответить
Leo
Ответить
![[Sims 4] Как сделать CAS красивее? / Мои любимые моды / Gshade [Sims 4] Как сделать CAS красивее? / Мои любимые моды / Gshade](https://ruvideo.cc/img/upload/QWdqZk5teFB5Y0M.jpg)