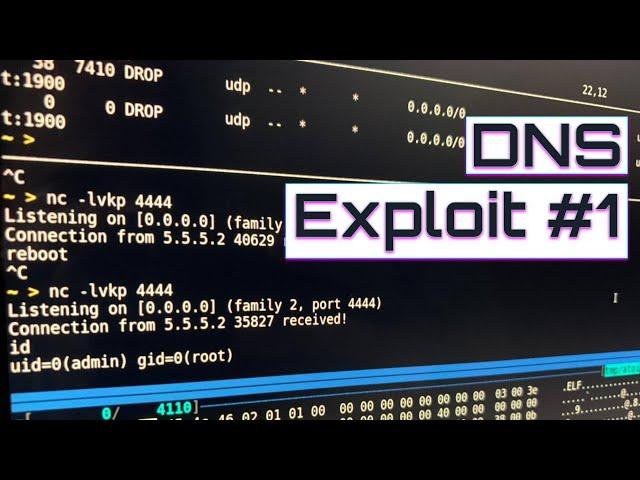
DNS Remote Code Execution: Finding the Vulnerability (Part 1)
Комментарии:

Nice video, added this to my watch list, will comeback and share my thoughts, for the time being its time to work.
Ответить
Excellent work! I want to test my router , Are the mips-static.tgz and the fuzz tool open source?
Ответить
lmao i love these videos you two are relatable yet much smarter...ive learned quite abit watching you guys thanks💯
Ответить
Great format. This is so clearly described and spoken that I listened to it a SECOND time, as a “podcast”. Thanks for going that extra “kilometer” and describing what’s on-screen.
Ответить
$4000 for the online course. I don't even have $40.
Ответить
I have a Question for Experts what I can not extract from that what is. My Provider had a Damage in a Knot where a Car crashed in.... first the internetconnection was lost, a few Minutes....after That it was ok for a few Minutes.... then it crashed again and was a longer Time out of Order. Since that I can not connect my Handy and my TV but every other Device works as usual. One Thing is that my Handy and the TV dont find the Port anymore... How is that possible?
Ответить
Can't wait for part 2! :)
Ответить
I'm surprised this is free.. This kind of walk-through is something you get from paid courses.
Ответить
I love how this video starts by explaining what LAN is, and 2 minutes later it's binary reverse eng
Ответить
I wonder what’s pornhub ? , going to check it out tonight
Ответить
what a nice research
Ответить
Crazy ammount of research, good job
Ответить
Sorry, can't talk right now, 200k people are hacking my LAN.
Ответить
Can't wait until the second part pops out. I really want to hit the ground running with this kind of exploitation
Ответить
Vamos 🔥🔥🎉
Ответить
Talk faster if you can please. It will only make good of your channel
Ответить
he's just showing off
Ответить
The best Pedro.
Ответить
No mamen están cabrones <3 (amazing work)
Ответить
Critters
Ответить
I feel like $20k is a paltry sum to pay hackers for a hardware (firmware?) Bug on a device sold to hundreds of thousands of people
Ответить
Awaiting part 2!
Ответить
part 2 ??
Ответить
Another piece of software that forgot to never trust user input 🙃
Ответить
I appreciate every video in this channel, This is very useful. Thank you, guys.
Ответить
Seeing my exact router in this vid is funny and terrifying
Ответить
Love your voice, is so soothing for teaching/learning. Thanks!
Ответить
Waiting for part 2! Amazing work!
Ответить
Zero dot zero dot zero dot zero… rofl
Ответить
I don't think I've ever said "Oh my God you can do that?!" so many times while watching a video haha. Amazing stuff
Ответить
Ha Ha HA, Hack PS5 if you can...
Ответить
guess all these kind of exploits wouldn't happen if we all used Rust XD
Ответить
DNS
DAS
닫힌문닫혀있는문
DZS
OPDZM
모래시계가작용하여연문

Thats another lvl...
Ответить
Where is the second part?
Ответить
hell I really appreciate what this guys are doing, because I don't understand 70% of what they are talking about. There is soooo much to learn and it seems scary 🤯
Ответить
Just another example of cops thinking they're above those they're supposed to serve
Ответить
I have no clue wtf your saying half the time but, I still watch hoping something will stick. something better than nothing, right? I love hearing the actual thought process of the hack as if you're going threw it for the first time. I like this very much.
Ответить
Regardless of the exploit, it's pretty disturbing that stock router firmware is spamming DNS requests to arbitrary commercial domains, just to blink an LED light...
Ответить
where is part2? ❤
Ответить
Incredible work. I'm blown away to see this entire research from start to finish, including the thought process. Well done. I hope to one day be able to do what you do!
Ответить
Wooowww amazing!!!! But how did you run MIPS executable on PC? Or you we're was on target via ssh?
Ответить
Thanks for sharing
Ответить
So awesome that you guys share this knowledge, really, keep up the great work!
Ответить
Thank you for this
Ответить
Exploit machine language x000x
Ответить









![Lyon, France travel vlog | Vieux Lyon, funicular ride, eating at a bouchon! Eurotrip pt4 [한국어cc] Lyon, France travel vlog | Vieux Lyon, funicular ride, eating at a bouchon! Eurotrip pt4 [한국어cc]](https://ruvideo.cc/img/upload/QVFxSjA0dXJFb2Q.jpg)