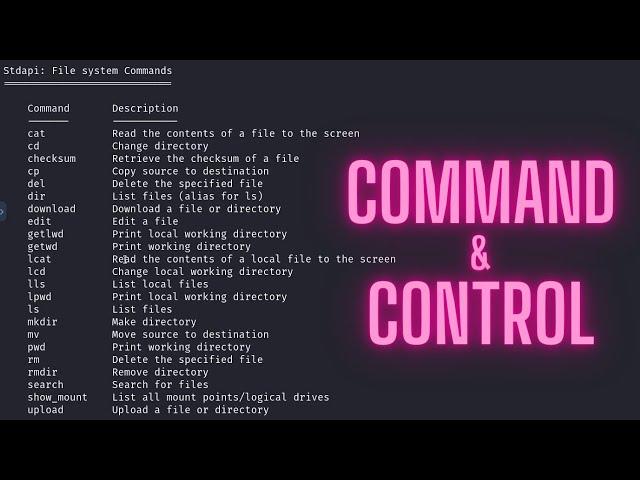
How to setup a C&C server with Metasploit like a Hacker!
In this video, I demonstrate how to setup a Command and Control (C&C) Server with Metasploit on Kasm workspaces.
Kasm is a container streaming platform that lets you run docker containers and stream them directly from your web browser. We first install Kali Linux inside Kasm Workspaces, setup tunneling with ngrok and then use Metasploit as a C&C server.
All the commands used in this video can be found in my blog post: https://www.blog.techraj156.com/post/setting-up-a-c-c-server-with-metasploit-and-kasm-workspaces
Metasploit: https://www.metasploit.com/
Kasm Workspaces: https://kasmweb.com/docs/latest/index.html
DISCLAIMER: This video is intended only for educational purposes.
The experiments in this video are performed in a controlled
lab setup and not on a live target. The content is purely
from a penetration testing perspective. I do not
condone or encourage any illegal activities.
Join my Discord: https://discord.gg/6TjBzgt
Follow me on Instagram: https://instagram.com/teja.techraj
Website: https://techraj156.com
Blog: https://blog.techraj156.com
Thanks for watching!
SUBSCRIBE for more videos!
Kasm is a container streaming platform that lets you run docker containers and stream them directly from your web browser. We first install Kali Linux inside Kasm Workspaces, setup tunneling with ngrok and then use Metasploit as a C&C server.
All the commands used in this video can be found in my blog post: https://www.blog.techraj156.com/post/setting-up-a-c-c-server-with-metasploit-and-kasm-workspaces
Metasploit: https://www.metasploit.com/
Kasm Workspaces: https://kasmweb.com/docs/latest/index.html
DISCLAIMER: This video is intended only for educational purposes.
The experiments in this video are performed in a controlled
lab setup and not on a live target. The content is purely
from a penetration testing perspective. I do not
condone or encourage any illegal activities.
Join my Discord: https://discord.gg/6TjBzgt
Follow me on Instagram: https://instagram.com/teja.techraj
Website: https://techraj156.com
Blog: https://blog.techraj156.com
Thanks for watching!
SUBSCRIBE for more videos!
Тэги:
#metasploit #kali_linux #reverse_shell #c&c #command_and_control #tech_raj #rce #ethical_hacking #penetration_testing #msfvenom #payloadКомментарии:
La Sala Metrologica ideale
ZEISS 3D Automation
Сборы перед ЧЕ 2023 (Днепр)
Станислав Бондарев
БРАТ 2: Подоляк і його родичі на рф
Самый сок
Pára Pedro. Filme de José Mendes. Divulgando a Tradição Gaúcha.
CARLINHOS STEINER☆ A música do Sul.
Jana Pallaske an studiVZ
ONE Deutschland
Практически догнал️
Aselerex
Подушки для ВТО. Мастер класс по пошиву + БОНУС колодка "грудь"
Клуб швей / Обучение шитью с нуля
Bike Theft with Angle Grinder and Threats of Violence
The Best Bike Lock