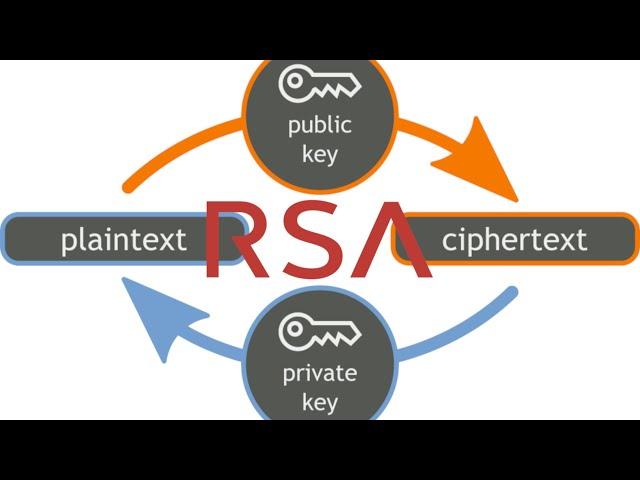
Комментарии:

thanks
Ответить
yeah yeah but still having the key they can still use it to decrypt it, by calculating the key, yeah i know, compute power, sure, goverment has the compute power, universities, and this is still really insecure, public and private keys my ass.
Ответить
an example would have been so useful
Ответить
Great explanation
Ответить
Nothing here
Ответить
Factoring primes is tough, but I think the greatest security the RSA algorithm provides isn't that. It's the incredible dullness of all known explanations of how it encrypts things.
Ответить
The relationship between private and public keys remains a mystery me.
Ответить
Adi shamir by his face looks jewish.
Ответить
diffie heilmann is so damn cool
Ответить
LMAO, literally watch your videos for fun. I never thought id see one of your videos when studying for classes.
Ответить
absolute dog crap explanation. didn't even go through any of the specifics.
Ответить
Not sure, i thought private was to decrypt, and public to encrypt. So you can encrypt using private as well?
Ответить
thanks for this video
Ответить
Hi , if somethink is crypted with rsa its mean can is have crypto ? I have some old hard driver from 2014 and at roming where is crypto file is show rsa and 3 file system with letter and numbers
Ответить
So basically in coding like c#, when the user 1 sends message, it uses its own public key to encrypt the data. User 2 which is receiver got private key of user 1 and use that to decrypt the data. If user 2 wants to send response back, jt uses its own public key to encrypt the data and user 1 would use the user 2 private key to decrypt the data.
Is this how it works??? But How both users get the keys???

thanx, i hope you do a video about SIT encryption for IOT it would be very helpful
Ответить
I like the reference to "Mean Girls"
Ответить
Finally I understand it!!! Great Thanks!
Ответить
Thanks for explaining this easy!
Ответить
Spot on.
You’d encrypt outgoing messages with the recipient’s public key
You’d encrypt with your private key for signature purposes. I’m not aware of any other reasons.
The whole idea with both encryption and hashing in general is that they’re easy to perform in one direction and exceedingly difficult in the other.

if the attacker got the alice public key, means attacker also can use it private key to decrypt ?
Ответить
thank u sir i have understood :3 <3
Ответить
How can enable encryption in Archer Control Panel
Ответить
Should be noted: DO NOT USE RSA. ESPECIALLY DO NOT ROLL YOUR OWN RSA IMPLEMENTATION. A large portion of modern crypto vulnerablities today are the result of programmers with no formal background in number theory using their own RSA because its math is deceptively simple to implement. The fact is that RSA is a minefield of mistakes waiting to happen be it not padding your ciphertext, using a too small public exponent, choosing primes that are too close or using primes that aren't securely generated, sending the same or similar messages encrypted with different keys, using the same prime for two different keys, the list goes on.
For asymetric encryption, it is strongly adviced that you use Elliptic curves, in particular Curve25519. The parameters of which have been carefully chosen by experienced cryptographers who know what they're doing.

Now normally what is used is diffie hellman key exange / eliptic curve to get a key, and with that key we use AES to encrypt the communications. RSA is used for certificates
Ответить
i always thought rsa stood for rosallosynthetic saedric almanation process
Ответить
PGP (GPG) next please !! 😆
Ответить
So, the private and public keys are interchangeable (math-wise) before you declare that one as private and one as public - correct?
Ответить
next gpg
Ответить
i like your "Works" series
Ответить
I like to think of the public key as a Lockable padlock, those kind in lockers that you can push in the shackle and it locks, but then you need the key to unlock it. thus the private key is the key, the padlock is that public one that anyone can use to lock their parcel in a cage with, and send it to you to open it
Ответить
Awesome! 2 likes for the video, a dislike for not including the lecture in the description.
- You total is 1 like, sir, have a nice day

Bro do you even calculate the area under elliptical curve?
Ответить
love from india bro 🇮🇳☮️
Ответить
I feel like one of my teachers will use this video in the future
Ответить
I would appreciate more visual aid in these videos. In my opinion it would make the videos more understandable and it would be easier to follow what you're talking about. Btw thanks for the educational content 👍
Ответить
Do a tutorial on how to encrypt your email with pgp. More people using it, the better.
Ответить
Yup bro a little demostration on terminal would also make this more understandable
Ответить
It's important to remember that you still have to be sure you got the right public key!
Maybe a video on roots of trust (for websites, secure boot, …) and their alternatives (safety number in Signal, networks of trust, etc.)?

If you want full understanding of the RSA cryptosystem (to the point of being able to program it), I advice reading "Introduction to Algorithms" (Cormen, Leiserson, Rivest, Stein) - the book also explains many related algorithms, like the Pollard Rho Method (generation of large, high-probability prime numbers).
Ответить
While AES is somewhat robust against quantum computers, RSA would be totally broken by it.
Ответить
Now I understand
Ответить
Thanks. Apriciate your work. Support from Italy
Ответить
Very good video.
Ответить