BSidesATL 2020 - Connect: Software Supply Chains and Code-to-Code Combat
Nearly every business today is a software business. Either software is delivered as a product to customers, or it is used internally for critical business operations. Internally used software could be as simple as operating system shell scripts that copy databases or automate network operations, or as complex as enterprise-wide business infrastructure like accounting or CRM systems. If unauthorized changes are made to this software, either deliberately by a bad actor, or accidentally through employee mistake, there could be severe consequences for the business.
Code signing has been used for 3 decades to prevent cybercriminals from tampering with delivered software. It’s been an effective technique – so much so that cybercriminals now steal code signing keys to thwart the process.
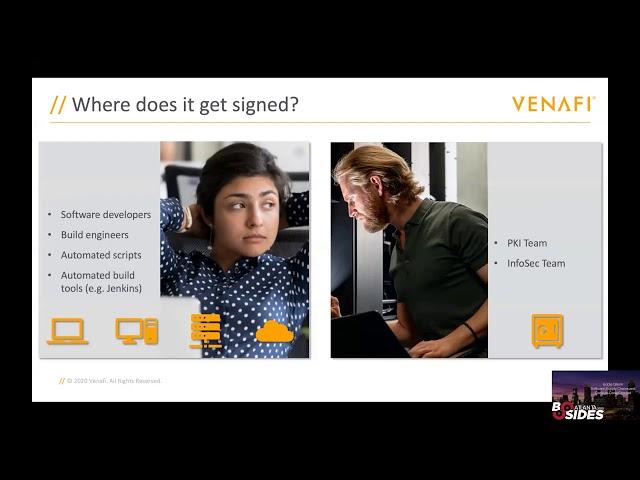
Even though many businesses use code signing to prevent tampering with software that they deliver to their customers, many may not use it to protect their internal software infrastructure. Usually this is because it is just too difficult to support the volume of people who need to code sign, too risky to provide this many people with private code signing keys, or there is a lack of PKI expertise in the groups responsible for building software infrastructure.
In this session we will examine the risks of not signing internal software infrastructure code and the common challenges that businesses face when trying to roll out code signing to large audiences. We will provide best practices for how to effectively do this which is convenient for end users as well as satisfies the needs of the security team.
Eddie Glenn is the senior threat intelligence manager at Venafi and is responsible for researching the risks and threats of code signing and endpoint infrastructure. Eddie has more than 30 years of experience in enterprise software at companies such as IBM, Rational, and Wind River where he held a variety of senior level positions in product management and product marketing. Eddie is co-author of the Definitive Guide to Next Generation Fraud and has written for various industry publications. He has a Bachelor of Science degree in computer and electrical engineering from the University of Virginia, and an MBA from the University of Oregon.
Code signing has been used for 3 decades to prevent cybercriminals from tampering with delivered software. It’s been an effective technique – so much so that cybercriminals now steal code signing keys to thwart the process.
Even though many businesses use code signing to prevent tampering with software that they deliver to their customers, many may not use it to protect their internal software infrastructure. Usually this is because it is just too difficult to support the volume of people who need to code sign, too risky to provide this many people with private code signing keys, or there is a lack of PKI expertise in the groups responsible for building software infrastructure.
In this session we will examine the risks of not signing internal software infrastructure code and the common challenges that businesses face when trying to roll out code signing to large audiences. We will provide best practices for how to effectively do this which is convenient for end users as well as satisfies the needs of the security team.
Eddie Glenn is the senior threat intelligence manager at Venafi and is responsible for researching the risks and threats of code signing and endpoint infrastructure. Eddie has more than 30 years of experience in enterprise software at companies such as IBM, Rational, and Wind River where he held a variety of senior level positions in product management and product marketing. Eddie is co-author of the Definitive Guide to Next Generation Fraud and has written for various industry publications. He has a Bachelor of Science degree in computer and electrical engineering from the University of Virginia, and an MBA from the University of Oregon.
Комментарии:
[ohhoho] 'BEST SHOT' Special Clip l 원호 WONHO
ohhoho 오호호
How to Crochet a Rose Flower | Beginner Crochet Tutorial
Lingzhi Handmade
Main Drag Music
rolandmedia

![[ohhoho] 'BEST SHOT' Special Clip l 원호 WONHO [ohhoho] 'BEST SHOT' Special Clip l 원호 WONHO](https://ruvideo.cc/img/upload/UWtfMWJReWc2dmk.jpg)








